Policy Solution Overview: (Study Note)Policy Solution in different Standards:•
3GPP Service-Based Local Policy (SBLP) –
PDF/PCC (See another study note - PCC)
•
3GPP2 Services Based Bearer Control (SBBC) - closely following 3GPP R7 Policy & Charging Control Architecture (PCC) where PCC provides access, resource, and QOS control
•
ETSI TISPAN – Resources Admission Control Subsystem (
RACS) for Wireline broadband accesses and network peering (See another study note - NASS+RACS)
•
ITU-T – Resources Admission Control Function (
RACF) for Wireless/Wireline broadband accesses, network peering with Explicit identification of Call Admission Control
•OMA (PEEM)
•Parlay (PM-SCS)
•IETF (PDP-PEP Model)What is Policy?"Policies" are implemented or executed within a particular context and can be represented at different levels, ranging from business goals to device-specific configuration parameters.
- Policy is a set of rules that governs the authorization, usage and charging for various resources in the network.
- Policies are rules that determine how a service request is handled
- Policies can be static (SLAs) or dynamic (per session)
- Policies can be edited: (1) manually, (2) based on time, (3) based on state
- Policies are interpreted by a rules engine
- Policy control is a highly complex area which presents some major challenges when making decisions about what to deploy and where.
The policies can apply to:- Policy management is used in the areas of network management where its application is necessitated by the tremendous complexity inherent in the administration and management of networking systems, in QoS management of differentiated networks, in resource and configuration management for network equipment such as routers, and in security management. The same general techniques can be available and applied in the management and delivery of enhanced services. Policy is a broad concept. In a service provider network policies can apply to: - Transport Routing (e.g. OSPF policies)
- Application Routing (e.g. Voice Call Continuity routing)
- Bandwidth allocation
- Firewall traversal
- Billing
- Security
- Identity
- Peering
- 3rd party partners
- Subscribers
- Users
- etc.
.jpg) PCC (Policy and Charging Control) functionality is comprised by
PCC (Policy and Charging Control) functionality is comprised by1) the functions of the Policy and Charging Enforcement Function (PCEF),
2) the Bearer Binding and Event Reporting Function (BBERF),
3) the Policy and Charging Rules Function (PCRF),
4) the Application Function (AF),
5) the Online Charging System (OCS),
6) the Offline Charging System (OFCS) and
7) the Subscription Profile Repository (SPR).
The related elements of policy management in architecture:
1) Policy Enforcement Point (PEP) - the place in a component that enforces the decision. Policy Enforcement must support and track the addition, modification, or removal of a resource (e.g. application, service enabler, and/or network element) as well as the policy associated with that resource.
The major policy enforcement functions:- Gating: block or admit flows
- Policing: limit the data rate of a flow.
- Marking: set specific bits in the IP, MPLS or Ethernet header of each packet of a flow to ensure that downstream switches and routers give the flow the required QoS treatment
- Metering & Charging: measure the total traffic volume (in bytes) or session duration for charging purposes
2) Policy Decision Point (PDP) - the component making the decision (as like a Rules Engine). Centralized policy management authorizes or denies requests for network resources made by any application or user based on business rules, user profiles, and/or network resource availability. Policy decisions are governed by the subscriber's policy profile as well as any network specific policies in the network the user is currently located.
3) Policy Execution Point - the place in a component actually performing the enforcement and can be merged with Policy Enforcement Point
4) Policy Repository - the component storing the policies
5) Policy Administration Point - for creating, checking policies
What is a Policy framework function (PMF)?- The decision point or function to control subscriber access to networks and services.
- How policies are reconciled between home and visited network, and where various policies are executed.
- Specific types of policies related to QoS, accounting, mobility (Presence enabled), packet flow optimization (P2P), and access (when at home, always WiFi).
- How policies integrate the network behavior with the applications being invoked.
Involves three major functions in the PMF- Policy decision function/ engine (like PDP/PCRF)
- Repository of policy rules (like SPR)
- Enforcement point (like PEP/PCEF)
ITU-T RACF:1) PD-FE – Policy Decision Functional Entity- Apply network policies to resource management requests from Service Control Functions
- Given an IP address pair and required BW, determine if the given flow can be supported in the network
- Manage resources along the flow path including NAPT Transversal and Gate Control
2) PE-FE – Policy Enforcement Functional Entity- Provides media path functions such as gate control / Firewall
- NAPT translation and Transversal
- Per flow policing and QoS-marking
- Can provide congestion/capacity information to Service Control
3) TRC-FE – Transport Resource Control Functional Entity- Connection Admission Control- Monitor network resource utilization and network topology to manage path bandwidth availability (reservation and/or monitor)
IETF PDP-PEP Model:- In the IETF model, the Policy Enforcement point acts as the policy requestor: Similar to the pull model in ITU and 3GPP standards
- IETF has developed protocols for the PDP-PEP interface: COPS, Diameter
PEP behavior:- Identifying requests that need an external authorization decision
- Ability to request for external authorization decision
- Enforcing the decision taken in the external authorization function
PDP behavior:- Receiving a request for taking a decision over an authorization
- Identify relevant policy and take a decision
- Return the decision
- May call delegated resources as part of the evaluation
OMA PEEM:PEEM specifies ways to convey and enforce policies that can be used to manage resources, processes, and underlying systems. PEEM enabler is driven by the need to reduce management complexity. Via
two patterns - proxy pattern or callable usage pattern, PEEM may interact with other resources.
The following is a list of
other elements that interact with PEEM:
1) Target Resource Requestor : Target Resource Requestor represents a resource (e.g. application, enabler) that issues a request to a target resource.
2) Target Resource : Target Resource represents the destination resource for a request made by another resource.
3) Delegated Resource : Delegated Resource represents the resource to which PEEM may delegate certain policy actions during the policy processing process.
4) Evaluation Requestor : Evaluation Requestor represents a resource (e.g. application, enabler) that issues a request for policy processing to PEEM.
5) Management Requestor : Management Requestor represents a resource (e.g. application, enabler) that issues a request for policy management to PEEM.
6) Interface to other resources : The interface to other resources is not specified by PEEM, but is used to exchange messages compliant to the interface of the target or delegated enablers or more generally messages compliant to the target or delegated resource interfaces.
The following is a list of PEEM components1) PEF (Policy Evaluation and Enforcement component) 1.1) PV (PEEM Evaluation).
- is responsible for the policy evaluation portion of the PEEM requirements. This component has the following features:
- identifies the policies associated with the request.,
- evaluates these policies using context information provided by the PEF requestor
- The PV component may use delegation to other resources where appropriate.
- returns, after completing all previous processing, the result of the evaluation to the PEF requestor.
1.2) PF (PEEM Enforcement)- is responsible for the policy enforcement portion of the PEEM requirements. This component has the following features:
- PF performs the "action" as a consequence of the result that was returned by PV (PEEM Evaluation component),
- The PF component may use delegation to other resources where appropriate
2) PM (Policy Management component)
- provides the functions of describing, creating, updating, deleting, provisioning and viewing of policies
3) Other entities:- PEF Requestor
- PM Requestor
- Other Resources
The PEEM enabler exposes the following interfaces:- PEM-1 (PEEM specified callable interface): is used by other resources to make a direct request for policy processing
- PEM-2 (PEEM specified management interface): is used by other resources to make a request for policy management.
- Proxy interface (used for intercepting requests to target resources): is used to exchange messages compliant to the target enablers or more generally messages compliant to combination of the target resource interface and the set of parameters that must be added to requests through that resource’s interface
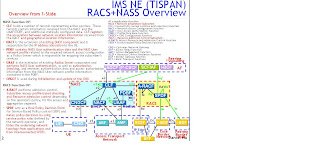
TISPAN RACS: See another study note - NASS+RACS
3GPP PDF/PCC: See another study note - PCCFurther Information: https://docs.google.com/fileview?id=F.57ac20ef-940b-4181-82f1-3024e6f03a12&hl=en
.jpg)
+(1-Slide).jpg)
.jpg)